CONFIDENTIALITY IN CYBER SECURITY EXPLAINED
In order to ensure confidentiality,We basically use 5 measures
· Encryption
· Access control
· Data masking
· Physical security measures
· Training and awareness
ENCRYPTION
Encryption comes with an encryption key that converts data to cipher text.this cipertext is not readable and can only be decrypted with decryption key .a way for ensuring the confidentiality of data.
ACCESS CONTROLS
Only the authorized can access the data by using passwords .
Data Masking
Method that involve obscuring data within the database to make it in accessible for unauthorized users while retaining the real data authenticity and use for authorized users.
A common example of data masking that we can see in day to day life is when we login to internet banking ,most of time we see few digits of our account no or credits cards nos as xxxxx and only last few digits are visible.
PHYSICAL SECURITY METHODS
Physical security is as the name suggest using physical means to protect the data.example biometric access in offices.
TRAINING AND AWARENESS is also a means that we can use to protect data confirdentiality.
Threat ,Vulnerability and Risk
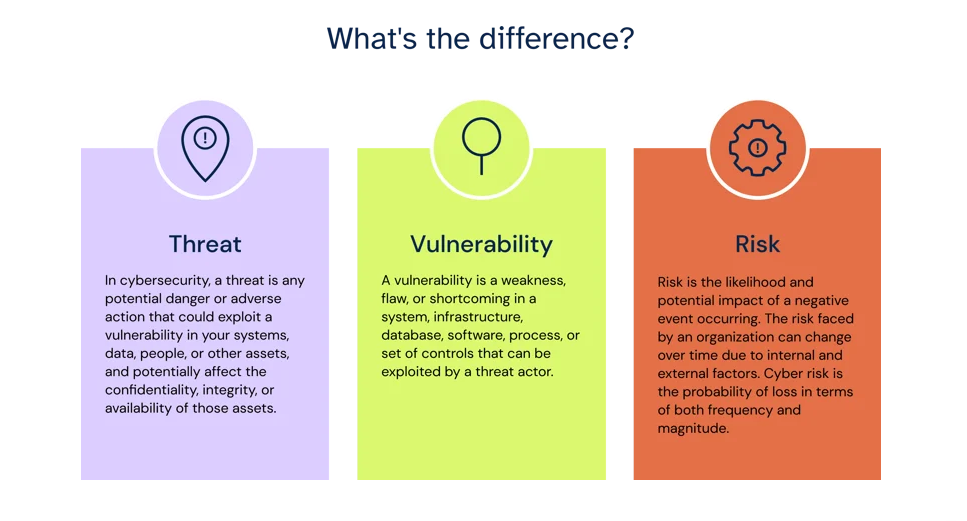
Just a small difference
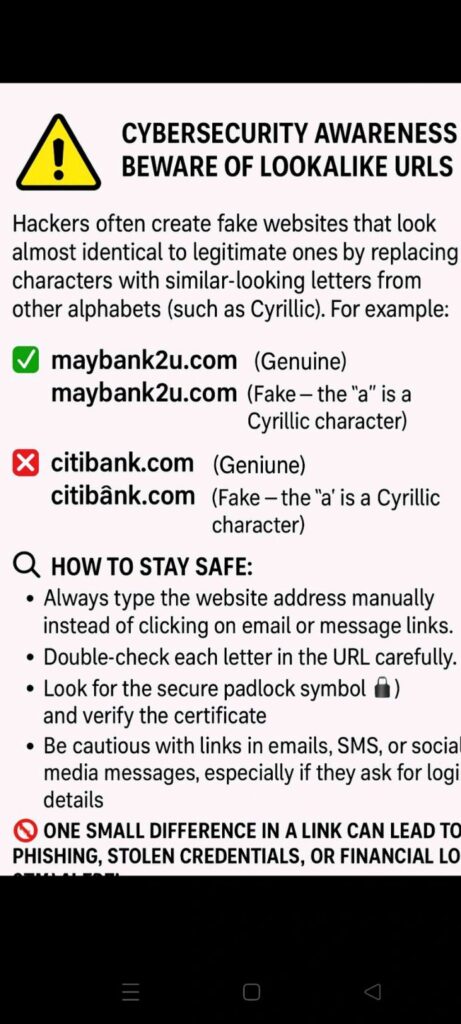
FUNDAMENTALS OF CYBER SECURITY – PART 1
FUNDAMENTALS OF SECURIYT: security vs convenience
SECURITY AND USABILITY GO AGAINST EACH OTHER.WHEN WE TRY TO MAKE SOME THING SECURE WE MAKE IT LITTLE DIFFICULT SO AS THE END USER WILL USE A VERY SECURE SYSTEM , JUST TO MAKE THINGS CONVENIENT TO USE .HE IS GOING TO BYPASS SOME SECURITY.
THINK OF IT AS WHEN WE TAKE INTERNET CONNECTION AND THE ENGINEER COME TO SETUP INTERNET , HE WILL MAKE A VERY SECURE PASSWORD AS 123SUx@HfW BUT ONCE HE LEAVES WE MAKE IT CONVIENT AS Johnwick@123 or Login@123 .so the point is security and usability go hand against hand. As a cyber security professional ,this is the biggest challenge that we are going to face as to make system more secure and more easily usable
First we will discuss the Two key terms in Cyber Security :
Information security: is Act of protecting data and information from unauthorized access , un lawful modifications and disruptions ,disclosure and corruption and destruction.
Information System Security: is protecting the system that contains this data ..examples protecting the data centers, smart phone, computers, servers.
3 pillars of security:CIA
confidentiality
integrity
availability
2 New things are added now Non repudiation and authentication
AAA
Authentication: Process of identifying the identity of a user or system .Authorization: Defines what actions or resources a user can access. Accounting: Act of tracking user activities and resource usage, typically for audit or billing purpose.
Security Controls: Measures or mechanisms put in place to mitigate risk and protect confidentiality , integrity and availability of information systems and data.
Security controls can be grouped into categories:
· Technical
· Managerial
· Operational
· Physical
Different type of security controls that we can have :
· Preventive
· Detective
· Compensating
· Deterrent
· Corrective
· Directive
ZERO TRUST
Security model that operates on the principle that no one ,whether inside or outside the organization ,should be trusted by default.